Compliance Policy Tool For Google Workspace
SysCloud offers out-of-the-box, customizable compliance policy templates to monitor inappropriate content in school-provided Google Workspace and identify violations of FERPA, CIPA, HIPAA, IEP, and PCI compliance.Compliance policy templates are part of SysCloud’s comprehensive data protection suite designed to help schools and institutions proactively protect privacy, safeguard confidential information and remain compliant with regulations.
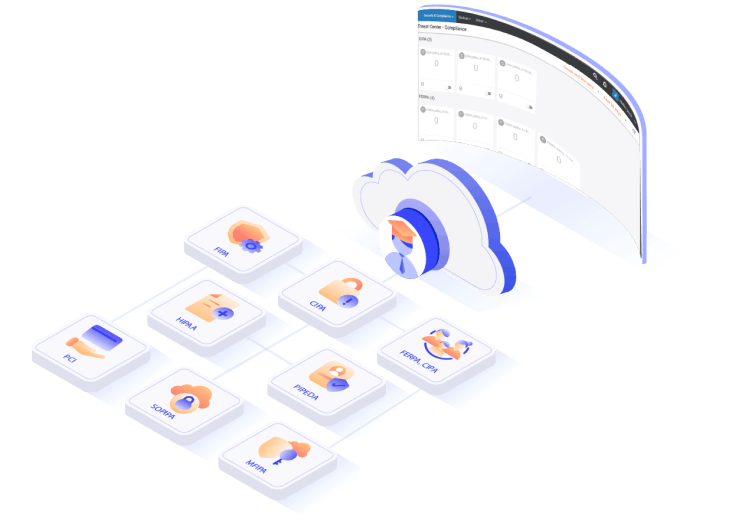
Why do you need SysCloud to manage compliance policies for cloud apps?
Policy restrictions
In Google Workspace, compliance policies are restricted to Google Drive, Gmail and Hangouts
Limited monitoring
The scope of monitoring is limited to PII data, credit card information, and the sharing of financial transaction data.
SysCloud includes all compliance regulations applicable to schools and institutions.
Compliance policy management - SysCloud vs. Google Workspace
Features | Syscloud | Google Workspace |
|---|---|---|
| PCI |  | |
| HIPAA |  | |
| PIPEDA |  | |
| CIPA |  | |
| FIPA |  | |
| MFIPA |  | |
| FERPA |  | |
| SOPIPA |  |
How does Syscloud ensure compliance in schools?
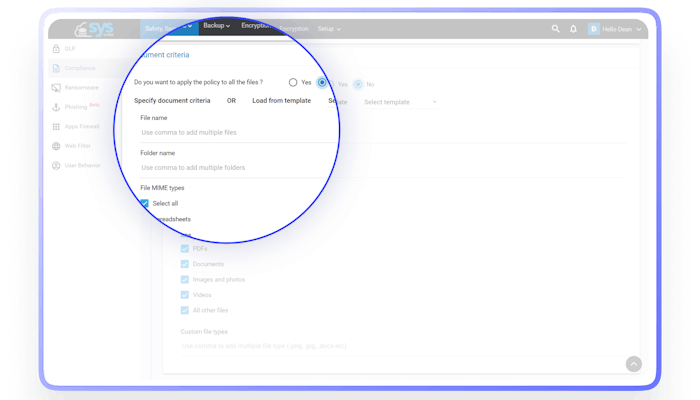
Flexible policy templates to dramatically improve your school’s compliance score
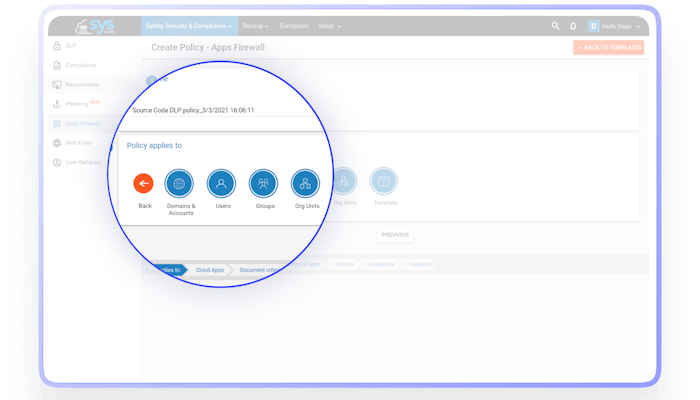
Get complete control on how users will be monitored for compliance
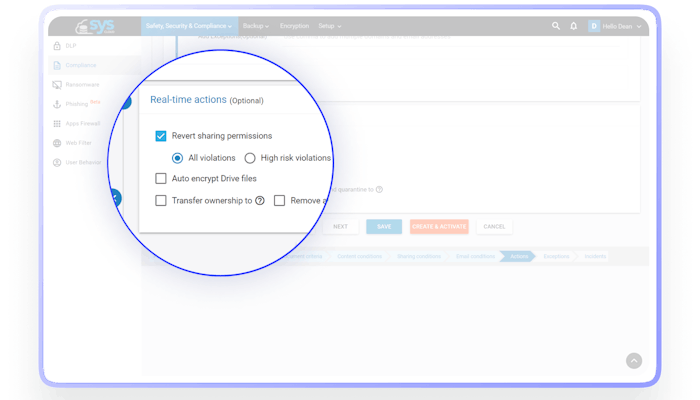
Define real-time actions for policy violations
How does Syscloud ensure compliance in schools?
Flexible policy templates to dramatically improve your school’s compliance score
Get complete control on how users will be monitored for compliance
Define real-time actions for policy violations

