Categories
In this article
- Introduction
- What makes Slack data vulnerable?
- How to stay secure in Slack?
Slack Security: Potential Risks and How to Stay Secure in Slack
15 Jun 2022
11 min read
Ahana
Article at a glance
- Public links and third-party apps pose significant data leakage risks if not properly managed.
Users can inadvertently expose sensitive information by creating public links or integrating unsecured apps. What is the solution?
Read more
Introduction
Slack is one of the most popular enterprise software for business communication with more than 12 million daily active users. Business users assume that conversations through direct messages and private channels on Slack will remain confidential and protected. However, there are significant security risks when using Slack for critical business communications.
2. What makes Slack data vulnerable?
2.1. The issue of encryption
2.2. Threat posed by third-party app integrations
In 2016, tech consulting firm 18F’s Slack account inadvertently exposed sensitive government information and resulted in a data breach. According to the report, over 100 General Services Administration’s (GSA) Google Drive accounts were accessible to outsiders for at least five months potentially exposing sensitive content such as personally identifiable information and contractor proprietary information. The breach occurred because the GSA had made the connection between the two apps using an authentication protocol known as “OAuth2.0,” which neither Slack nor the GSA’s IT standards had approved.

2.3. Power vested to the owner and admins in Slack
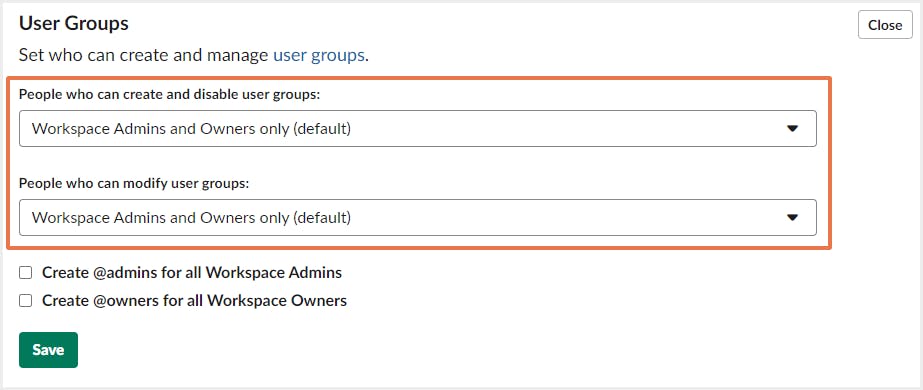
1. Slack admins can allow everyone in the company, except guests, to create, modify, and disable user groups.
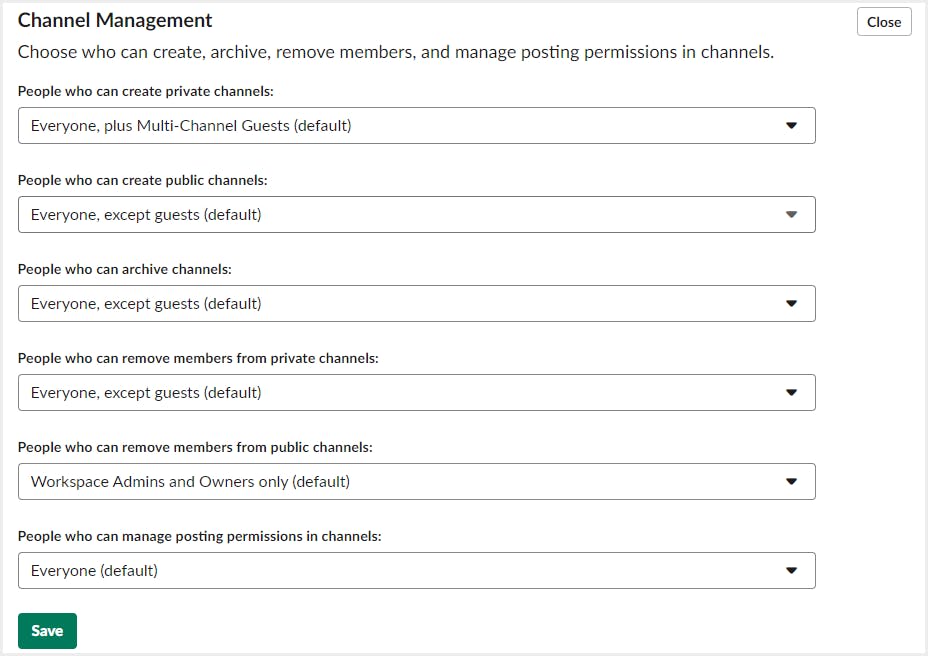
2. Slack admins can allow everyone to create, archive, and remove members from channels.
3. Slack admins can allow workspace members to override the retention settings for private channel messages and direct messages.
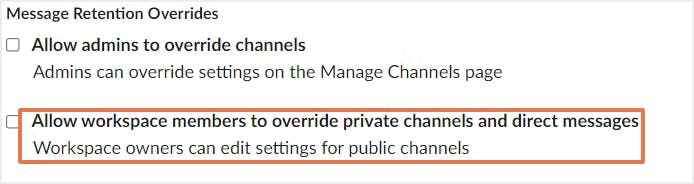
2.4. Risk of posting malicious content to Slack
For example, in April 2016, Ars Technica reported that, “A surprisingly large number of developers are posting their Slack login credentials to GitHub and other public websites, a practice that in many cases allows anyone to surreptitiously eavesdrop on their conversations and download proprietary data exchanged over the chat service.”
Joining publicly accessible Slack groups may also present a data leakage risk. In February 2018, the Origin Report’s Josh Fraser shared that the 1,118 members of its open Slack community had their personal information — including their email addresses, usernames, real names, profile pictures, last updated timestamps, and time zone settings — exposed by a hacker who manipulated API keys.
2.5. End users can create public links to files
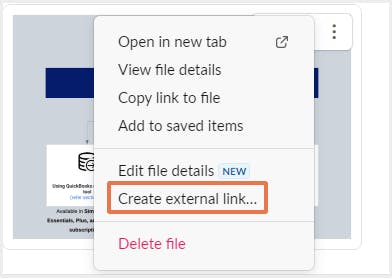
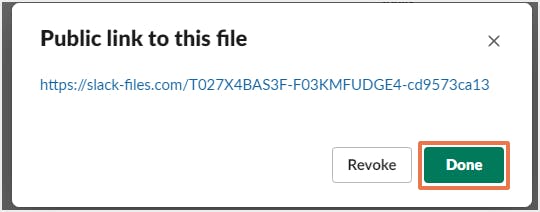
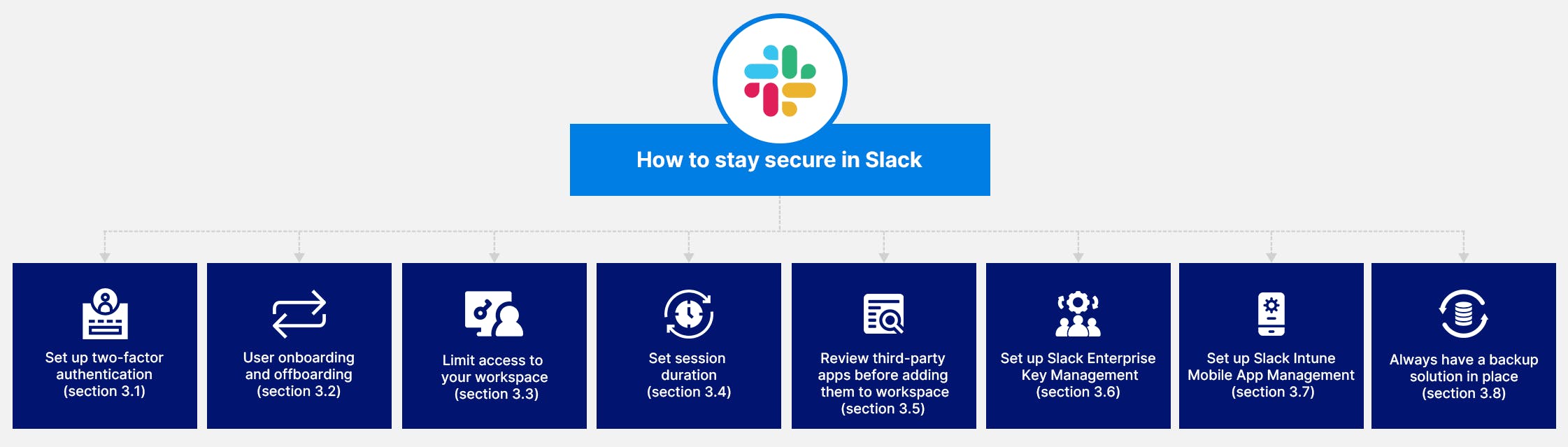
3. How to stay secure in Slack?
3.1. Set up two-factor authentication
3.1.1. How to set up 2FA in Slack
Step 1: Sign into the workspace and select Settings and Administration and click on Workspace settings. Then select Account and Profile.
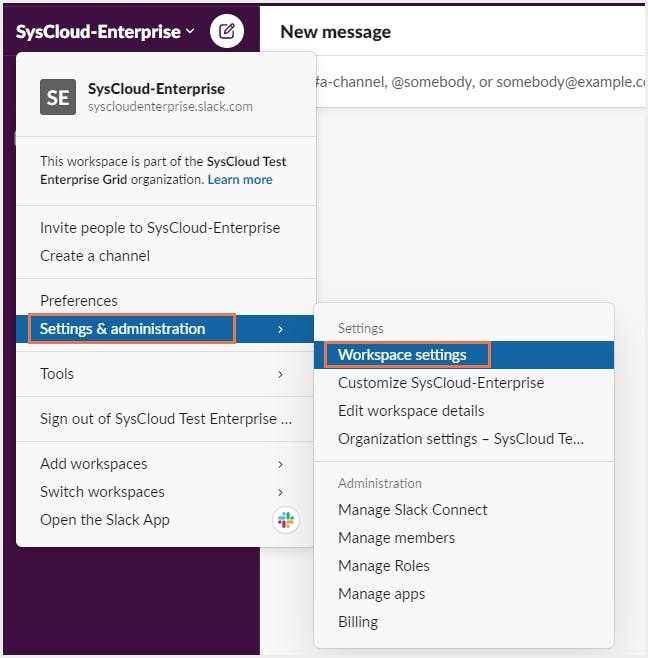
Step 2: Next to Two-factor Authentication, click Expand. Then, click Set Up Two-Factor Authentication.
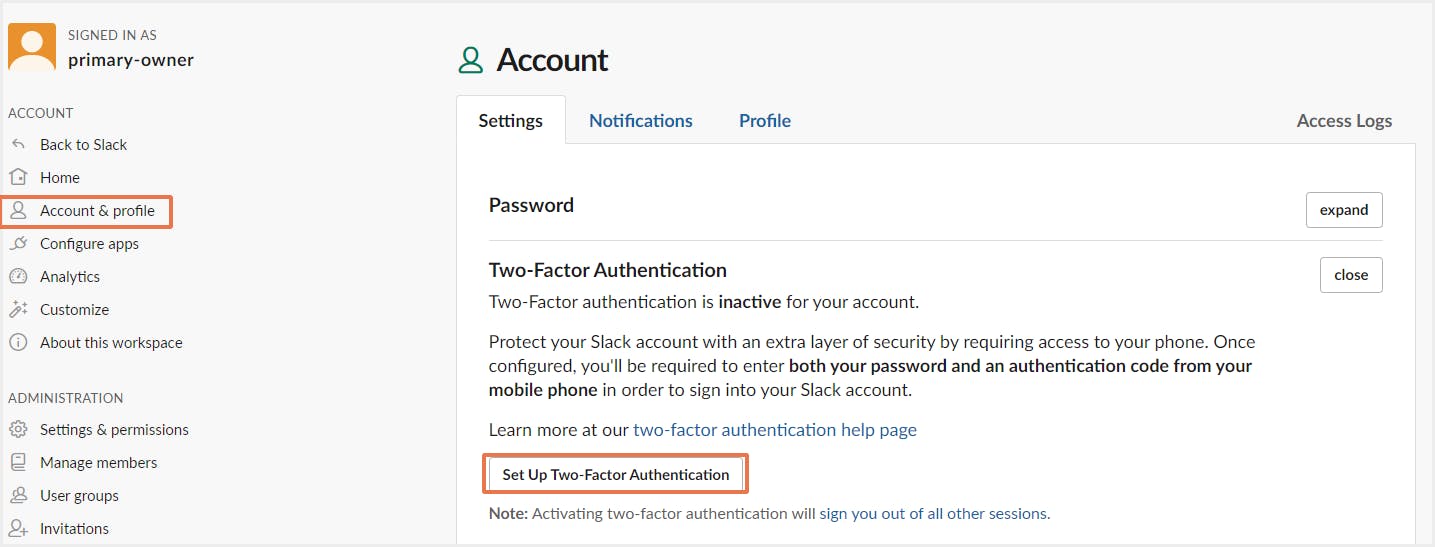
Step 3: Enter your password and click SMS Text Message to receive authentication codes by text message
Step 4: Select your country from the menu. If your country isn't listed, choose Other.
Step 5: Enter your mobile phone number, including your area and/or zone code.
Step 6: Slack will send a 6-digit verification code to your device. Enter the code on the Slack 2FA configuration page.
Step 7: To finish, select Verify Code.
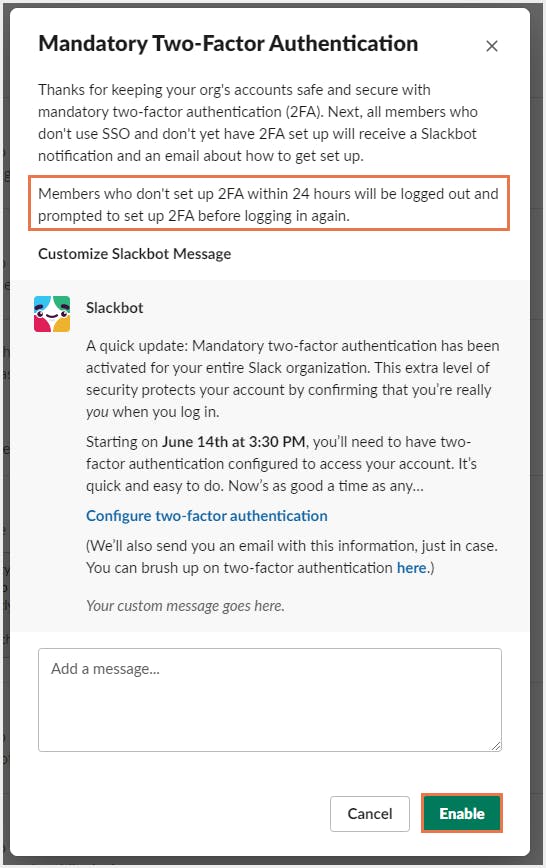
3.2. Set up user onboarding and offboarding
3.3. Limit access to your workspace
3.3.1. Limit access to workspace by managing admin approval for invitations
Step 1: From your desktop, click your workspace name in the top left.
Step 2: Select Settings & administration from the menu, then click Workspace settings.

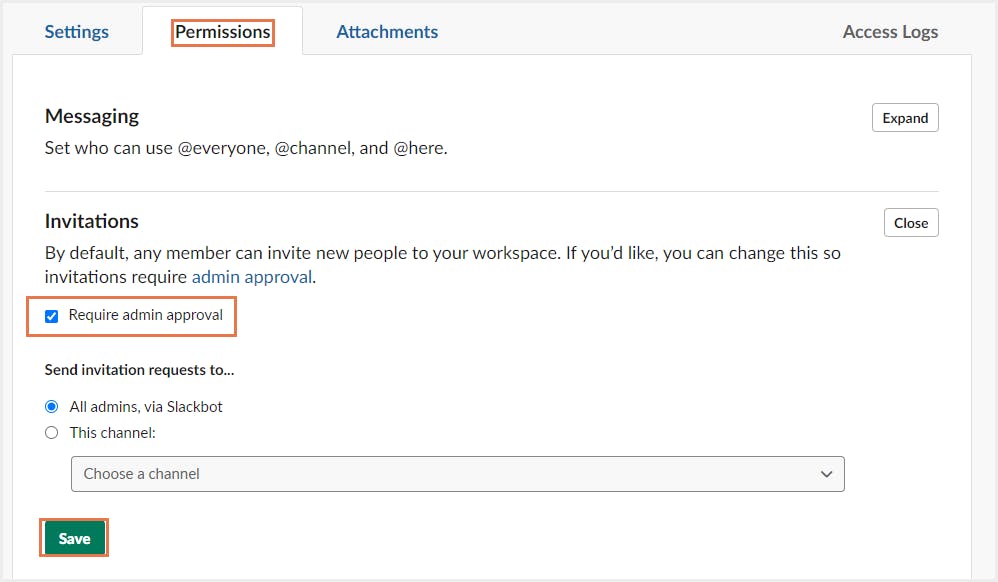
Step 3: Click the Permissions tab.
Step 4: Next to Invitations, click Expand.
Step 5: Check or uncheck the box next to Require admin approval. Click Save.
3.3.2. Deactivate members’ accounts that no longer need access
Step 1: Click your workspace name in the top left.
Step 2: Select Settings & administration from the menu, then click Manage members.
Step 3: Click the three dots icon to the right of the member you’d like to deactivate.
Step 4: Select Deactivate account.
Note: On the Enterprise Grid plan, users can only be removed at an organization level. Click here to know how to deactivate a user’s account from an Enterprise Grid subscription.
3.4. Set session duration
3.4.1. How to set up session duration
a) For Pro and Business+ plans:
Step 1: From your desktop, click your workspace name in the top left.
Step 2: Select Settings & administration from the menu, then click Workspace settings.
Step 3: Click Authentication.
Step 4: Next to Session Duration, click Expand.
Step 5: Select how much time should elapse before requiring members to sign back in.
Step 6: Click Save.
b) For Enterprise Grid plan:
Step 1: From your desktop, click your workspace name in the top left.
Step 2: Select Settings & administration from the menu, then click Organization settings.
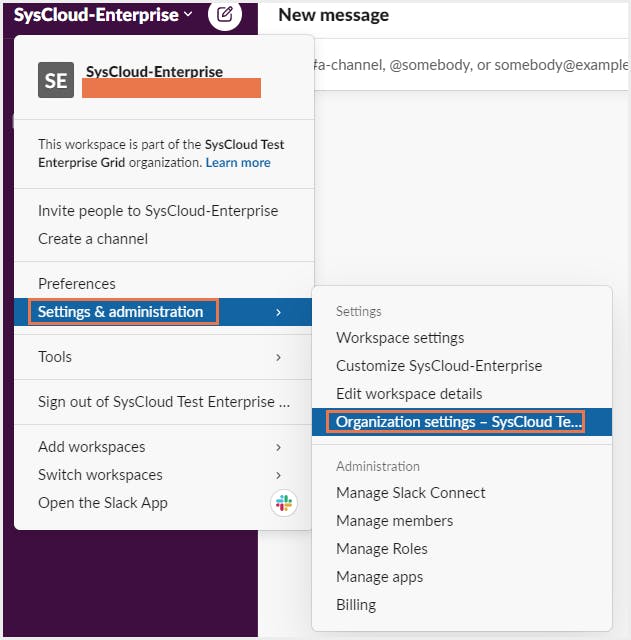
Step 3: Click 🔒Security in the left column, then select Security Settings.
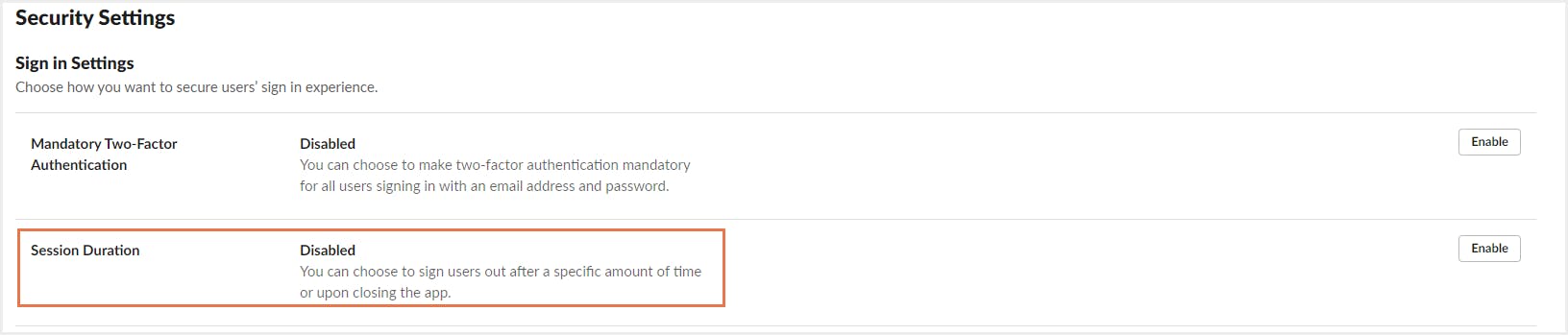
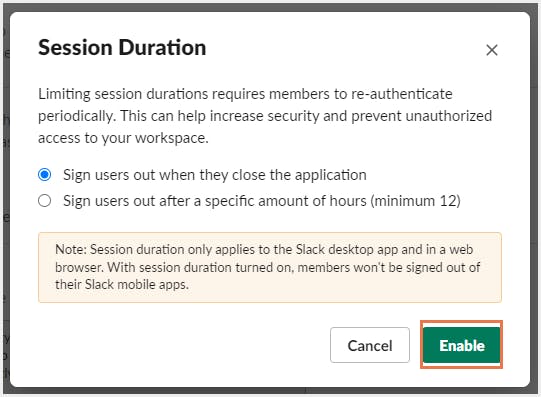
Step 4: Next to Session Duration, click Enable.
Step 5: Select how much time should elapse before requiring members to re-authenticate.
Step 6: Click Enable.
3.5. Evaluate third-party apps before adding them to Slack Workspace
Understand the app permissions required: Each of the third-party services connected to Slack has a unique set of permissions that tells what information can the app access, and how it can use that information. By default, third-party apps can do the following in Slack:
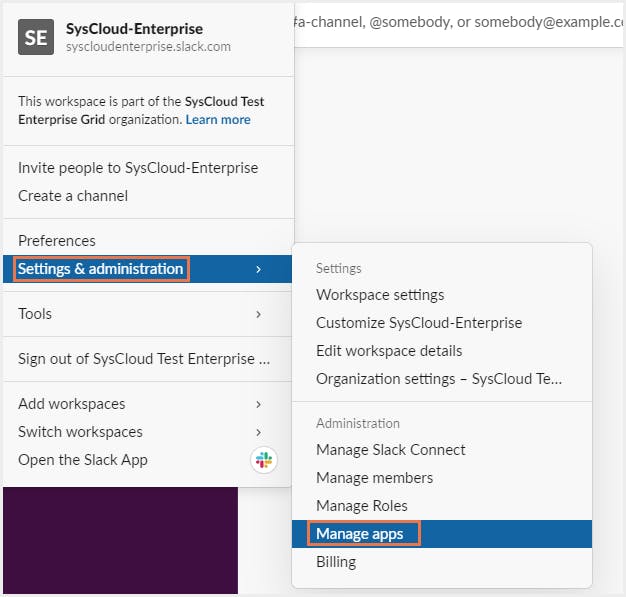
Step 1: Click on the Slack workspace name in the top left.
Step 2: From the menu, select Settings and Administration and click on Manage Apps to open App Directory.
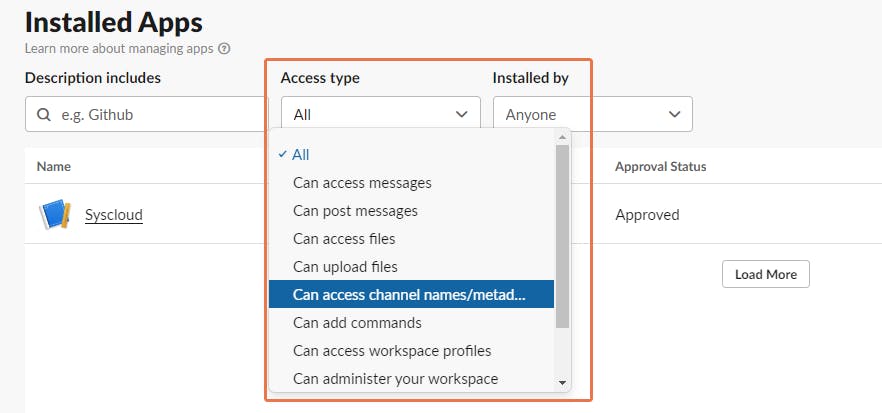
Step 3: Click on Apps and select Installed apps, Approved apps, or Restricted apps.
Step 4:Click on the drop-down menu below Access types to view apps with different access types.
2. Manage app approval for your workspace: Workspace owners can enable app approval to restrict or pre-approve certain apps for Slack data security.
Step 1: Click on your workspace name in the top left.
Step 2: Select Settings & administration from the menu, then click on Manage apps to open the Slack App Directory.

Step 3: Click App management settings in the left column.
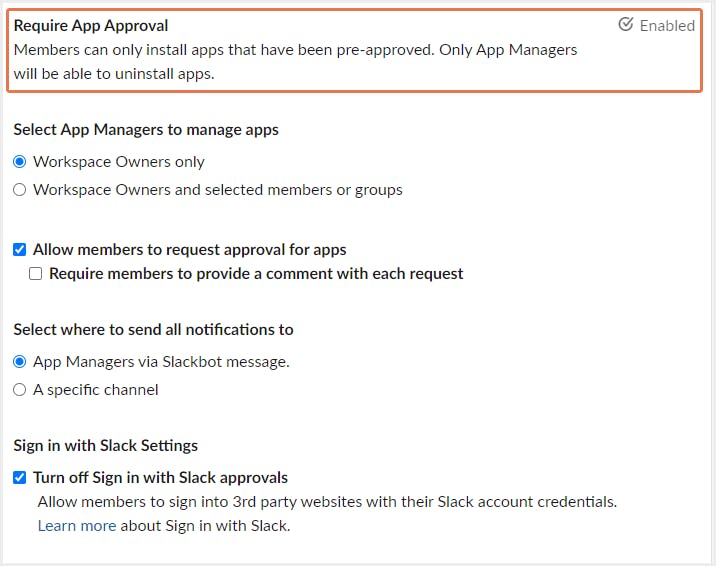
Step 4: Click the toggle next to Require app approval to enable the setting.
3.6. Slack Enterprise Key Management
3.7. Slack for Intune Mobile App management
Learn more about MIAM here
3.8. Always have a backup solution in place
Third-party backup applications like SysCloud can be used to effortlessly backup and restore your Slack data. SysCloud backup allows admins to back up, restore, and export Slack channel conversations and files whenever needed.
3.8.1. Why should you use SysCloud to back up Slack data?
- Automated Slack backups and automatically resolves API errors.
- Export threads, channels, direct messages, or even the entire workspace in JSON format.
- Restore threads in direct messages and channels with a single click.
- Search for content inside conversations, files, channels, and user groups using keywords, across all your workspaces.
To learn more about SysCloud’s backup for Slack, click here.
Recommended Content
30 March 2022
5 min read
29 Mar 2022
7 min read
30 Mar 2022
10 min read
In this article
- Introduction
- What makes Slack data vulnerable?
- How to stay secure in Slack?

